IDP.ALEXA.51 is one of such viruses that might interfere with the usual work of the system and open a backdoor, permitting a hacker to access the device and collect all required information. This virus has been detected by Avast, Avira and AVG antivirus suites firstly detected in 2016. Researchers has been reported that this malicious threat often infiltrates the system during the installation of various Flash games – such as SeaMonkeys, Plants vs. zombies, etc. Reports have been continuously updated since the IDP.ALEXA.51 virus is found by some of the…
Read MoreMonth: October 2019
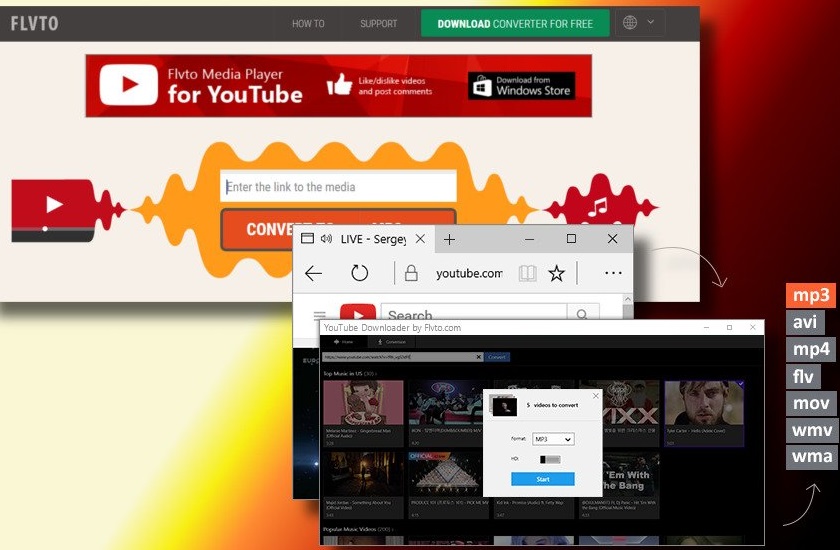
How to remove Flvto.biz virus
Flvto.biz redirect is most of the time caused either by malicious advertisements on the site you visit or adware. It could be blocked on a specific website by using a free browser extension like Adblock. These malicious adware are generally clustered with other free programs that you download from the website you visit. Symptoms of Flvto.biz malware Once an adware is intruded into your computer through the installation of your program, your browser will be redirected to Flvto.biz and other sites. You can look after some of the symptoms mentioned…
Read MoreBest strategies for ransomware protection
Ransomware has a vicious effect on the target system. Even the best of the antimalware program can’t prevent their intrusion. Unlike other malware, Ransomware has a unique way to manipulate its victims. It generally encrypts all the files of the target system and then demands a certain amount of ransom (probably in the monetary form) to decrypt the file. According to the authentic source, every year ransomware targets millions of systems around the globe. The cost of protecting critical systems against the ransomware has been rapidly thriving every passing day.…
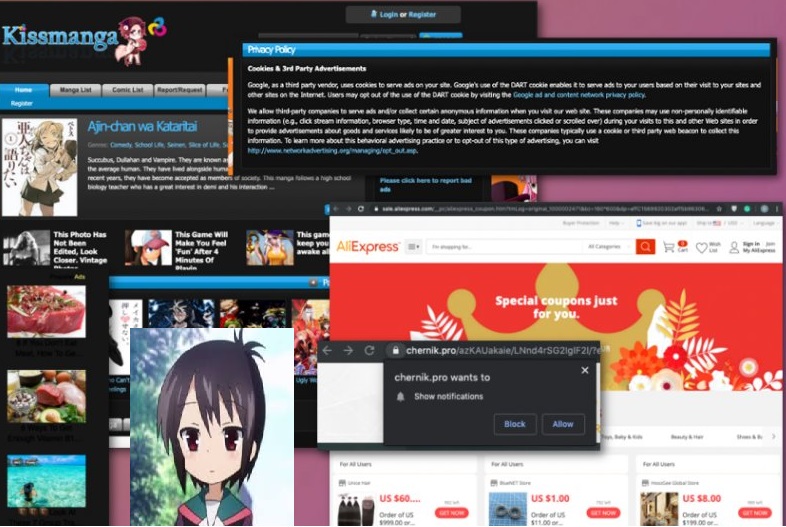
Read MoreHow to remove Kissmanga malware?
Well! Kissmanga is widely discussed to be a group of websites having issues of malware infections due to the tons of suspicious and malicious advertisements. This Kissmanga service is associated with many ad-supported sites and advertisers directly; hence the website is filled with commercial pop-ups, banners, etc. The websites mainly include video game commercials, promotional material for software, etc. Once, if users clicked on any kinds of banners shown on the website would let them to redirect to different website and tons of several windows open on the browser slowing…
Read MoreA Fake Russian Tor Browser Steals $40,000 in Bitcoin
Cyber security firm ESET have unveiled a malicious version of the Tor browser – a program used to access the dark web. And it has been stealing user’s Bitcoin. According to the firm, the illicit actors were able to steal $40,000 in BTC. A Trojan effected version of an official Tor browser has been used by the scammers which redirects users to two websites that claim the user’s version of Tor is out of date even if it has been updated timely. When a user clicks on the “Update” on…
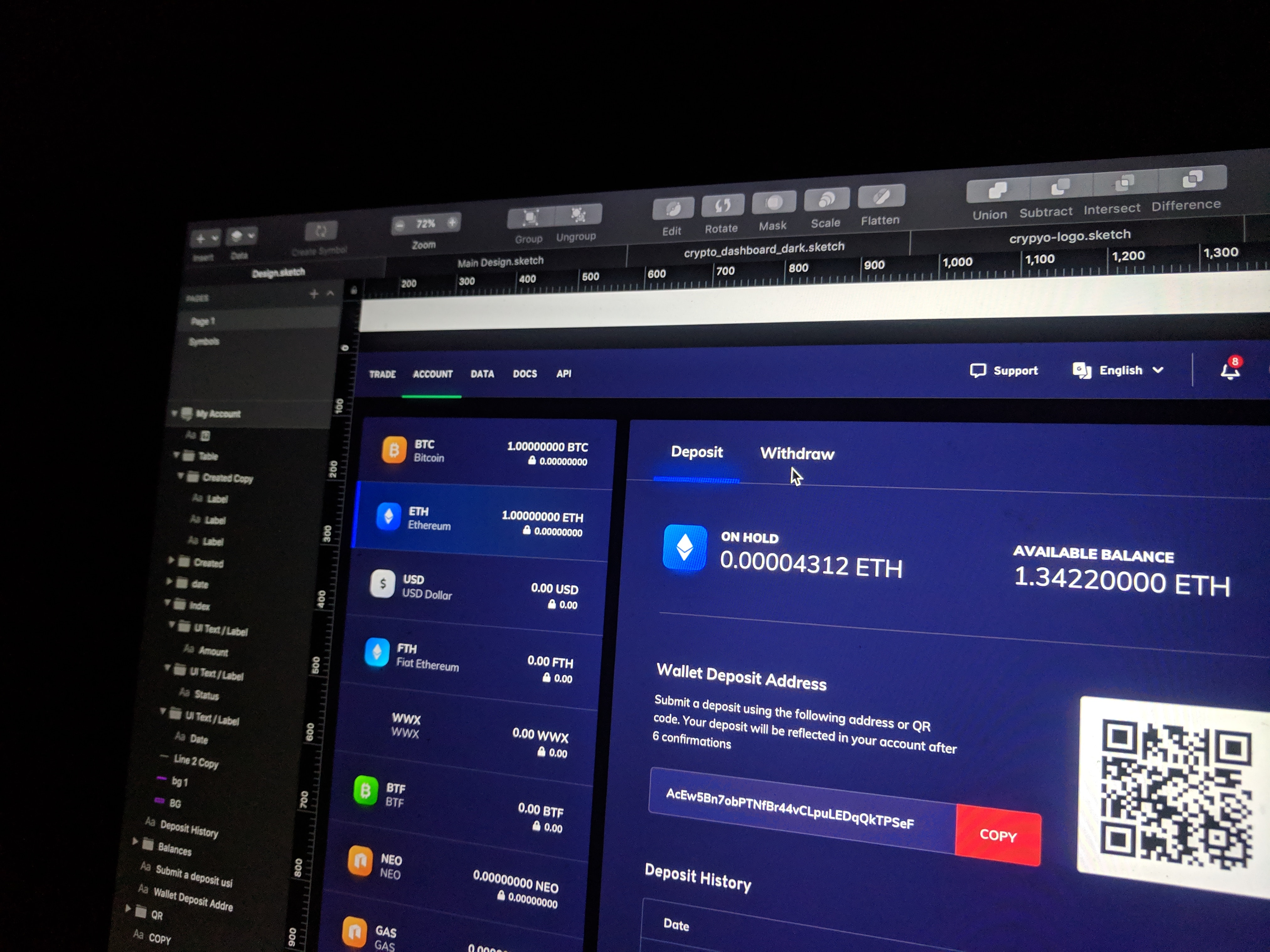
Read MoreHow Attackers Create Crypto Trading Scheme to Install Malware?
Attackers have been built an elaborate scheme to disperse a crypto-currency trading program that installs a backdoor on a victim’s Windows PC or Mac. This has been discovered by a security researcher MalwareHunterTeam, where an attacker has created a fake company offering a free crypto-currency trading platform called JMT Trader. And it infects the victim with a backdoor Trojan when this program is being installed. How the Crypto Trading Malware Scheme being Created This scheme starts with a professionally designed web site where the attackers encourage the JMT Trader program,…
Read MoreHow to Detect and Prevent Crypto Mining Malware?
Hackers are moving to opt for crypto-jacking infecting IT infrastructure with crypto mining software to have a stable, reliable, constant revenue stream. As a result, they are getting very smart in hiding their malware. CoinHive is an online service that provides cryptocurrency miners, in other words, crypto-mining malware that can be installed on several websites using JavaScript. The JavaScript miner runs in the browser of the website visitors and mines coins on the blockchain. It is promoted as an alternative to placing advertising on the website which is being used…
Read MoreGoogle Needs All Android Phones Approved to Run on Android 10
Reportedly, Google has been launched Android 10 approving all smartphones to be run on it after January 31, 2020. According to Google’s GMS – Google Mobile Services – documents accessed by XDA Developers, Google has made it mandatory for all smartphone makers to ship new smartphones approved with the latest version of the company’s mobile operating system. GMS is essentially a suite of Google apps, services, and libraries that has to be licensed by smartphone makers because it enables them to pre-install Google Play Store and Google Play Services on…
Read MoreHow Smominru Botnet Malware is Infecting Windows PCs?
According to the report published by cybersecurity firm, Guardicore Labs, a viral Botnet malware, Smominru, has been detected frequently as one of the most spreading entities affecting the Windows operating system across the world. And also the Botnet has been affecting nearly 4,700 PCs every day, with over 90,000 PCs affected worldwide in just August itself. One of the main reasons for PC networks being affected is due to the failure of the company administrators unable to patch their servers and PC networks. However, it also affects various firms due…
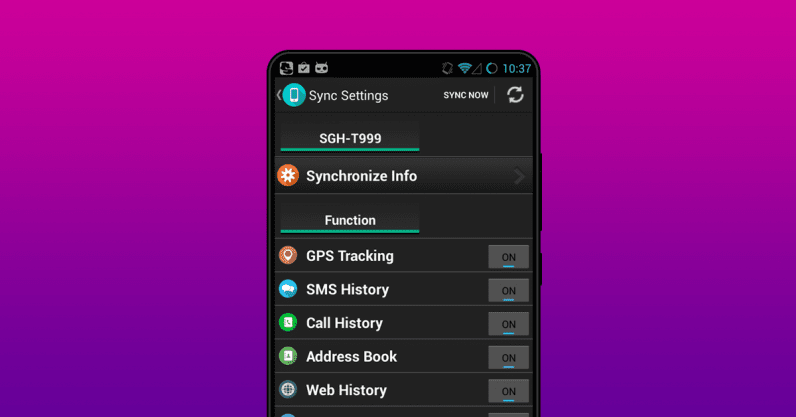
Read More373% Growth in Android Spying Stalkerware Apps
Stalkerware apps are generally used to spy on users’ call information, messages, and GPS locations. And it has been increased an overwhelming 373% during the first eight months of 2019 when compared to the same period the year before. This has been discovered by cybersecurity firm Kaspersky when most of the prominent regions around the world have affected due to its illicit nature. Stalkerware apps have been exposed and publicly criticized many times, yet in most countries, their presence has prevailed. According to its functionality, these apps, firstly, are…
Read More